Beyond the Web Application Hacker’s Handbook (Advanced)
Course Summary
For many years, the Web Application Hacker’s Handbook has been the de facto resource for professional web application assessments. The authors have run training courses based on this book for over 10 years, for thousands in the field.
However, we believe today’s readers can find numerous online examples and labs which cover the basics.
This course is for the professional who can churn through 5-10 day application assessments but has not followed up on key areas to build their career and abilities further. This target professional is likely to resonate with the below:
- Always meant to use burp macros;
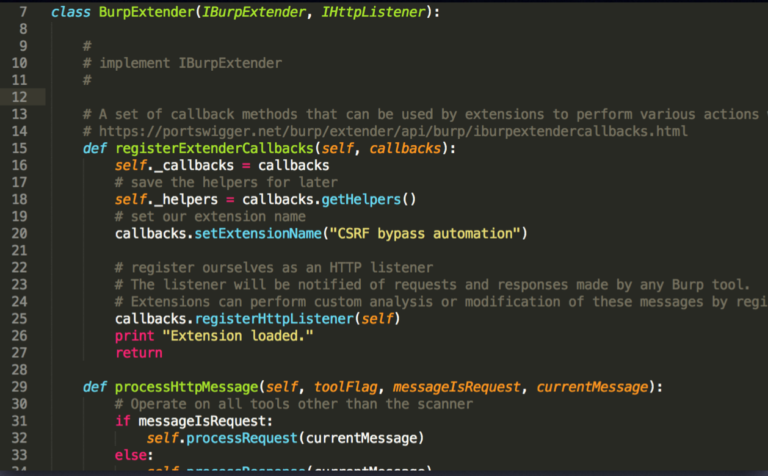
- Kept meaning to get around to writing Burp Suite extensions;
- Read about SSTI, blind XXE and Java deserialisation but not done the deep dive;
- Looking for new technologies to target and logic puzzles to solve, but keeps running into the same material (and same online CTFs).
Course Abstract
This course focuses on giving delegates the grounding in tooling, methodology and experience to take on areas of an application which may previously have felt out of reach on a short-term assessment. If you have been in professional application security assessment for over a year or so, you will likely empathise with the issues at the heart of the “Course Contents” shown below.
We assume a common body of knowledge (the OWASP Top 10, HTTP protocol, HTML, JavaScript and basic programming abilities) and aim to immediately build on this with variants and more complex testing environments which we will overcome together in the classroom.
Course Contents
You can get the quickest feel for what’s on the course, by understanding what we do not cover: no SQL injection, XSS, traversal… This is not a course on basics that you can find elsewhere; in fact, we can give delegates free access outside of the course to our previous labs server with over 400 examples in all of these common areas. This will allow us to focus on areas you will not have encountered elsewhere.

Modules
- Testing “untestable” Applications: learn how to deal with what may have seemed deal-breakers in the past such as reactive session termination, custom data encapsulation schemes, CSRF and other obstacles to testing;
- Assessing Rare Technologies: develop an approach to fuzzing, fingerprinting, researching and exploiting any of the rarer technologies that you might encounter;
- Deep Exploitation: cover hot topics that deserve a deep dive such as Java Deserialisation, External Entity Injection (XXE), and Server Side Template Injection (SSTI) and Server Side Request Forgery (SSRF);
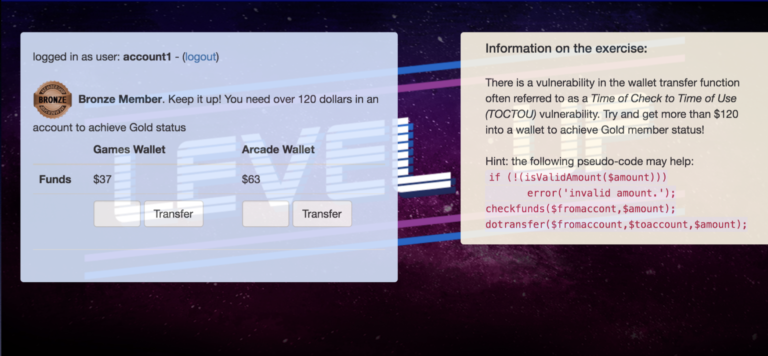 Exploiting Encryption: understand the ways in which the use of hashing and encryption may be flawed, and how you can overcome it;
Exploiting Encryption: understand the ways in which the use of hashing and encryption may be flawed, and how you can overcome it;- Breaking Logic: learn to identify the common logic flaws due to developers’ assumptions or non-comprehensive coverage of application behaviour.
Who should take this course?
The course is designed to provide additional capabilities and learning for appsec professionals who can already achieve general security coverage of a web application.
Delegates will be expected to have practical experience of the OWASP Top 10, HTTP, HTML, JavaScript and the basics of a scripting language such as Python (or any other language).